 SECURITY
SECURITY
 SECURITY
SECURITY

 SECURITY
SECURITY
Cybersecurity threats continue to plague cloud infrastructures, and sadly these threats are still mostly the same from years’ past.
But just because these threats continue doesn’t mean that cloud security, taken as a whole tapestry, isn’t as secure as on-premises equipment. That debate — which seems to have spanned a decade or more — should be put to rest forever. Two things many information technology managers have learned are that data center technology doesn’t age well, and it also accumulates tremendous technical debt, the implied cost of future reworking required when problems need to be fixed or approaches become less useful over time.
Take the case of the Southwire Co. LLC, which makes electrical cabling — ironically, the kind of cabling that is installed in hyperscale cloud facilities. The 70-plus-year-old company has about two-thirds of its infrastructure mostly in Google Cloud, and that proportion continues to increase.
“We are now focused on a cloud-first direction,” Southwire Chief Information Officer Dan Stuart told SiliconANGLE. “We realized that the cloud was more secure in general, and we were able to better segregate and secure our operational technology that we have on our shop floors from our overall IT infrastructure.” Stuart pointed out the intrinsic security controls that Google Cloud Platform uses, supplemented with Palo Alto Networks Inc.’s Prisma Cloud products.
But despite these generalities, securing the cloud is all about the details, and getting these right will take some effort.
In this analysis, we present five broad categories, describe some of the more notable exploits of the recent past, and provide recommendations for how to avoid them in the future. To compile this data, we used several reports, including Wiz Inc.’s State of the Cloud for 2023, based on scans of more than 200,000 cloud customer accounts, the Cloud Security Alliance’s Top Threats to Cloud Computing survey of 700 industry experts in June 2022, and Palo Alto Networks’ Unit42 Cloud Threat Report using data from tens of thousands of sensors across their customers’ networks in April 2023.
Here’s what organizations looking to protect their cloud infrastructure need to consider:
Cloud providers are constantly adding new cloud services, and with those services come bushels full of new application programming interfaces to connect them together. For example, according to the Wiz report, Amazon Web Services Inc. has added APIs at a steady pace, with about 40 new services and 1,600 new actions per year for the past six years. Moreover, the CSA report notes that “APIs and microservices must be checked for vulnerabilities due to misconfiguration, poor coding practices, a lack of authentication and inappropriate authorization.”
But tracking the way APIs are consumed by applications, configuring them properly and ultimately securing them is hard, as Peloton found out a few years ago when its leaky API exposed private data of its customers. Although it did scan its applications for potential vulnerabilities, it chose to ignore the recommendations of the security firm that found them.
“Leaked credentials are also central to every cloud breach we analyzed,” said Unit 42’s report. Finding and eliminating hard-coded access credentials becomes a lot more difficult when you have dozens of different cloud services and thousands of virtual machine instances to examine.
Why do these hard-coded credentials still exist? Mainly because of lazy DevOps practices, such as providing full access rights to the entire enterprise source code repositories. Unit 42’s report found that more than 80% of their customers used hard-coded credentials in their source control management tools.
The best way to eliminate hard-coded credentials is to scan code at runtime. There are a number of secret management tools such as HashiCorp Vault and Cloudflare Inc.’s Secrets Store. “In order for developers to build at high velocity and for security administrators to feel at ease, companies need to adopt a highly reliable and secure secrets manager,” said Cloudflare Inc. product manager Dina Kozlov. That is a good first step.
There is also a new service from Trail of Bits called trusted publishing that helps authenticate code being posted to open-source repositories by using more trusted credentials. “Trusted publishing eliminates the need for long-lived API tokens and passwords, reducing the risk of supply chain attacks and credential leaks while also streamlining release workflows. Critical packages on PyPI are already using trusted publishing to make their release processes more secure,” according to its announcement.
In addition, Netskope Inc. has a series of recommendations in its latest threat report that can help stop some of these leaks, such as better inspection of downloaded files to prevent malware intrusions and blocking downloads entirely from untrusted or unused apps and from newly minted domains and risky file types.
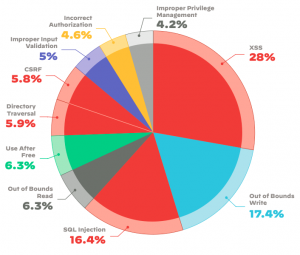 I wrote my first story about the perils of SQL injection more than 20 years ago, and even demonstrated how anyone using a simple Google search could pull this off. Sadly, things haven’t changed. Unit42’s report found these two old chestnuts are still ranked in the top three most disclosed types of vulnerabilities in their report.
I wrote my first story about the perils of SQL injection more than 20 years ago, and even demonstrated how anyone using a simple Google search could pull this off. Sadly, things haven’t changed. Unit42’s report found these two old chestnuts are still ranked in the top three most disclosed types of vulnerabilities in their report.
In this pie chart (adjacent) they show the total universe of disclosed vulnerabilities last year, with the red slices highlighting ones that are relevant to web or API applications. The report points out that the growth of these exploits continues and mentions the now-infamous web-based attacks on SolarWinds that continue to this day: “Even a year after its first disclosure, we still see an increasing trend of exploitation attempts,” the authors wrote.
Securing against these exploits is easy enough to talk about: Have better input screening, understand your app infrastructure, monitor and firewall network egress traffic, and use better DNS security to block potentially malicious domains, recommendations that Netskope mentioned in its report. However, these basic tactics are notoriously difficult to universally deploy, as the number of SQLi and XSS exploits demonstrate.
Securing a cloud estate requires need different tools and techniques than securing on-premises equipment. “Traditional digital forensics and incident response techniques are not designed to handle cloud breaches because the tooling, processes, and data sources necessary for investigating security incidents are very different between on-premises and cloud environments,” said Unit42’s report.
It cites the average time to resolve a security alert across all its customers is about six days, with half of them taking more than four days. “This represents a lengthy window of opportunity for potential adversaries to exploit a newly discovered vulnerability,” the authors wrote.
But six days is even a conservative figure. Consider a recent announcement from Toyota. It announced that data of more than 2 million customers has been available online for more than 10 years because of a misconfigured cloud storage bucket. And Barracuda Networks Inc. has had its own breach since last October and only recently found and fixed it.
Implementing a fix here isn’t simple. We just need better tools that are designed from the ground up with the cloud assets in mind. Should organizations focus on API and credentials, shared code supply chains, insecure services and containers, exposed databases? Maybe all of the above.
One solution is this cloud-based anomaly detection system using Bytewax and Redpanda for an AWS cloud collection. Another is a new Red Hat Inc. service to improve things called Trusted Software Supply Chain. And though many security teams employ honeynets to help spot and stop intrusions, a better mousetrap could be this interesting development on the use of what is called honey tokens in software supply chains.
Cloud providers often cite that infrastructure security means understanding the split concerning who owns what between the customer and the provider, as discussed in a post on CSOonline. That is a complete cop-out, and one of the reasons why there are still issues with cloud security.
The problem with a shared-ownership security model is that the lines are blurred for how this sharing takes place, and exploits and disasters result from when there are mistakes in communication and responsibilities. Also, “ensuring each developer understands its company’s assumptions of shared responsibilities with the cloud provider requires education,” as the CSA report illustrates in its discussion of who applies software patches and other mitigations once a vulnerability has been discovered.
Take the 2019 case of a breach of Capital One’s AWS infrastructure by a malicious insider, as examined in detail in this post on Diginomica written by Kurt Marko. Capital One had misconfigured some firewall rules on AWS, but AWS also shares some blame because of how its cloud services setup that made them vulnerable to server-side request forgeries.
To make the shared-responsibility model work properly, those blurry lines need better resolution and careful delineation. The CSOonline post provides some solid suggestions on how to obtain more clarity. Playbooks on patching and scanning for potential problems should lay out exactly who does what and when, and these roles should be practiced in tabletop security exercises too.
Finally, there’s perhaps the most vexing issue with cloud security: the numerous ways identity and access management can make or break security. This issue topped the CSA threat list, and numerous analysts have continued to highlight the problem over the years.
Sure, the news will continue to focus on insecure cloud storage buckets, but the real problems run much deeper. For example, how organizations roll out multifactor authentication matters, if it’s even used at all.
Unit 42’s report found that more than half of its customers don’t enforce MFA for users with admin rights on their main web cloud consoles that manage their entire infrastructure. Then there is the issue of which particular MFA tech should be used for the additional factors, such as hardware keys, passkeys and biometrics. Although most experts agree on what organizations need to steer clear of — such as SMS onetime passwords — the devil is in the details.
Certainly the move toward working from home has made identity management more complex, putting more of a burden on the information technology department to verify employees, customers and partners.
The best step forward toward getting the identity problem under control should be using a cloud-native application protection platform. That post also outlines some specific tactics to improve identity management.
The bottom line: There is a lot more work to do to secure an entire cloud estate. And these are just five broad categories that aren’t necessarily exclusive or exhaustive.
As Chris Vickery, a senior risk assessment specialist at Backblaze Inc., told SiliconANGLE, “There’s a common rule of thumb that has not changed: Any software, with a sufficiently large number of users that can be misconfigured will be misconfigured by some percentage of those users. The legacy cloud platforms have not yet addressed this inescapable reality.”
So how can those threats be reduced? Vickey recommends as one mechanism having better ways for outside researchers to report potential problems to an enterprise’s security team.
THANK YOU